Using the 700wl Series System
• Create a variation of the default “Unauthenticated” Access Policy that includes the same access rights
(which basically only allow a client to request authentication) but set the NAT option to
When
Necessary
and the addressing option to Require DHCP. In the example, this is named
“UnauthenticatedRealIP”
• Make sure that the Access Policies you define for clients matching your target VLANs have the NAT
option set to
When Necessary and the addressing option to Require DHCP. In the example in
Figure 2-15 these are named “VLAN10clientRights” and “VLAN20clientRights.”
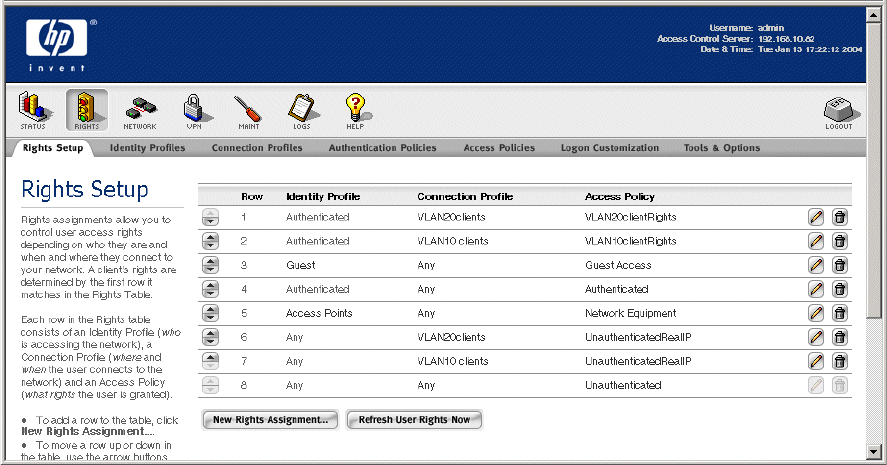
• Create two new rows in the Rights table directly above the default row for Unauthenticated clients
to map clients that match your new Connection Profiles to your new “UnauthenticatedRealIP”
Access Policy (rows 6 and 7 in
Figure 2-15).
Figure 2-15. Rights Table Providing VLAN Matching for Unauthenticated Clients
Now, when an unknown client connects via Slot 1 Port 1, with traffic tagged as VLAN 10, that client will
match Connection Profile “VLAN10clients” and based on the “UnauthenticatedRealIP” Access Policy,
will receive a real IP address in the 192.168.150.x range. Clients that connect through port 2 and whose
traffic is tagged as VLAN 2 will receive real IP addresses in the 192.168.156.x address range.
Any unknown clients that connect through port 1 that are not in VLAN 10, or through port 2 that are
not in VLAN 20, will only match the bottom row of the Rights table. They are associated with the
original “Unauthenticated” Access Policy, and will receive a NAT IP address provided you left the
“Unauthenticated” Access Policy unchanged so that it specifies NAT
Always.
The limitation is that clients in VLAN 10 will receive an address in the desired subnet range only if they
connect through port 1, and clients in VLAN 20 will receive the correct address only if they connect
through port 2. In any other situation, those clients will not receive an IP address in the specified range
despite the presence of the correct VLAN tag in their packets. Note that you can configure the system
so that these clients do receive access rights based on the VLAN ID as described in the first example
shown in
Figure 2-14.
HP ProCurve Secure Access 700wl Series Management and Configuration Guide 2-27
