Chapter 7 Public-Key Operations 247
Performing DSA Operations
Step 2: Setting The Algorithm Object
To verify the signature created here, use the same AI:
Step 3: Init
Associate a key and algorithm method with the algorithm object through
B_VerifyInit. The Chapter 4 Reference Manual entry on this function shows that it
takes four arguments: the algorithm object, a key object, an algorithm chooser, and a
surrender context. The algorithm object in this example is
dsaVerifier
. For a key
object, you want to use a DSA public key, presumably the partner to the DSA private
key used to sign. Build an algorithm chooser; the elements are the AMs listed in the
Reference Manual Chapter 2 entry for the AI in use.
B_VerifyInit is fast, so it is
reasonable to pass a properly cast
NULL_PTR for the surrender context:
Step 4: Update
Digest the data that was signed with B_VerifyUpdate; the prototype of this is in
Chapter 4 of the Reference Manual. Unless there is an extraordinarily large amount of
data (for example, a megabyte or more), this function is quick and a
NULL_PTR for the
surrender context will probably be no problem. Assuming you have the same input
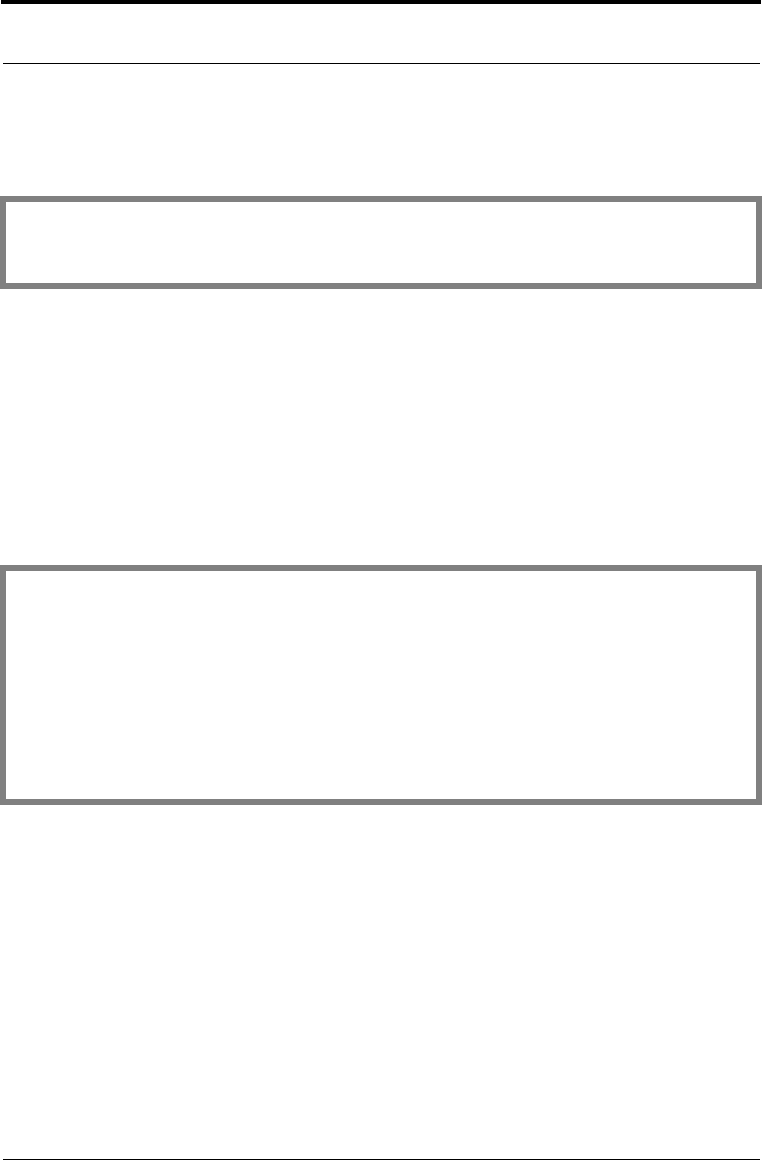
if ((status = B_SetAlgorithmInfo
(dsaVerifier, AI_DSAWithSHA1, NULL_PTR)) != 0)
break;
B_ALGORITHM_METHOD *DSA_VERIFY_CHOOSER[] = {
&AM_SHA1,
&AM_DSA_VERIFY,
(B_ALGORITHM_METHOD *)NULL_PTR
};
if ((status = B_VerifyInit
(dsaVerifier, dsaPublicKey, DSA_VERIFY_CHOOSER,
(A_SURRENDER_CTX *)NULL_PTR)) != 0)
break;
