Cryptography Overview
44 RSA BSAFE Crypto-C Developer’s Guide
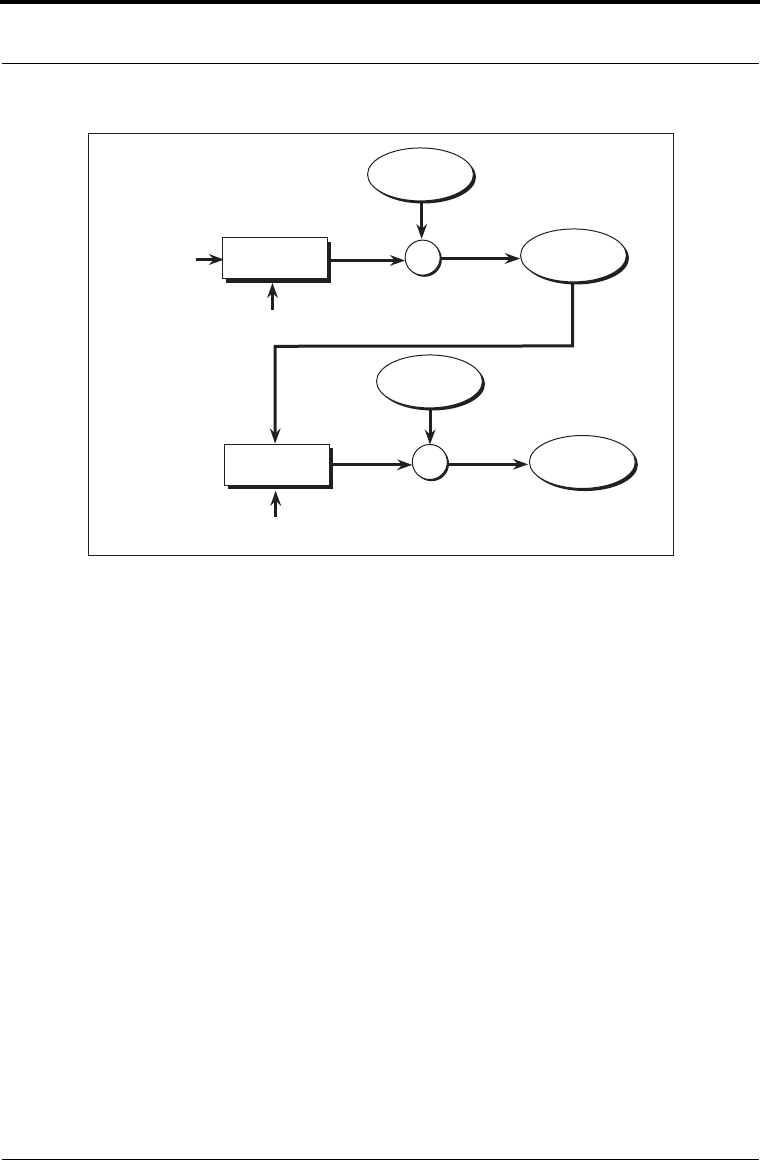
Figure 3-5 Cipher Feedback (CFB) Mode
To encrypt plaintext using CFB mode:
1. Generate your key and your IV.
2. Encrypt the IV with the key to get a block of output, B
1
.
3. XOR B
1
with the first block of your plaintext, P
1
, to get the first block of
ciphertext, C
1
.
4. Encrypt C
1
with the key to get the second block of output, B
2
.
5. XOR B
2
with the second block of your plaintext message, P
2
, to get the second
block of ciphertext, C
2
.
6. Repeat Steps 4 and 5 until the entire text is encrypted.
To decrypt the ciphertext, the decryptor uses the same (secret) key and initialization
vector and follows the same sequence of steps.
CFB mode does not require padding. If your data length is not a multiple of the block
size, simply truncate the final block of output to be the same size as the final segment
of the data, and then XOR it. You can use CFB mode to encrypt a stream of data.
2nd message
block
2nd cipher
block
Key (K)
Block Cipher
Initialization
Vector (IV)
1st message
block
1st cipher
block
XOR
Block Cipher
Key (K)
XOR
P
1
B
1
B
2
C
1
C
2
P
2
