SYSTEM ARCHITECTURE
3.4.4 Page Protection
Systems that do not make extensive use of
segments can instead protect pages. (Page protec-
tion can also be applied to sections of large
segments.) Like a descriptor, a page table entry
has a set of protection attributes; the
80386
checks every reference to the page for confor-
mance to these attributes.
A page table entry can
be
marked with one of
two privilege levels, user or supervisor. User
level
corresponds to privilege
level
3 but supervisor
pages can only be accessed
by
tasks running at
privilege
levels
0,
I,
or
2.
A user page can also
be
marked read-only or readable-and-writable.
The
80386 checks a page's protection attributes
after verifying that an access
is
consistent with
the segment attributes. Thus, page protection
is
a
convenient way for an operating system to apply
additional protection to portions
of
a segment.
For
example,
an
operating system can safely
store task-related operating system data, such as
page tables and
file
descriptors, in a task's data
segment
by
making the containing pages super-
VISor
pages.
3.5
System Calls
Most operating systems organize their services as
a collection of procedures that tasks can call. An
unprotected
80386 operating system can place its
procedures and application code in a level 0 code
segment
(or
more than one such segment);
an
application task can then invoke an operating
system service with
an
ordinary Call instruction.
Such
an
approach
is
fast but relies on the
application tasks to
be
error-free and
well-
behaved (as they are in embedded systems, for
example). Nothing prevents a task running at
level
0 from calling an address that
is
not
an
operating system entry point; nor
is
such a task
prevented from corrupting operating system
data.
To
protect the operating system, application
code and data can be placed in less-privileged
privileged segments. Just as a task running at a
3-13
given privilege
level
cannot read or write a more
privileged data segment or page, neither can a
task directly call a more privileged code segment.
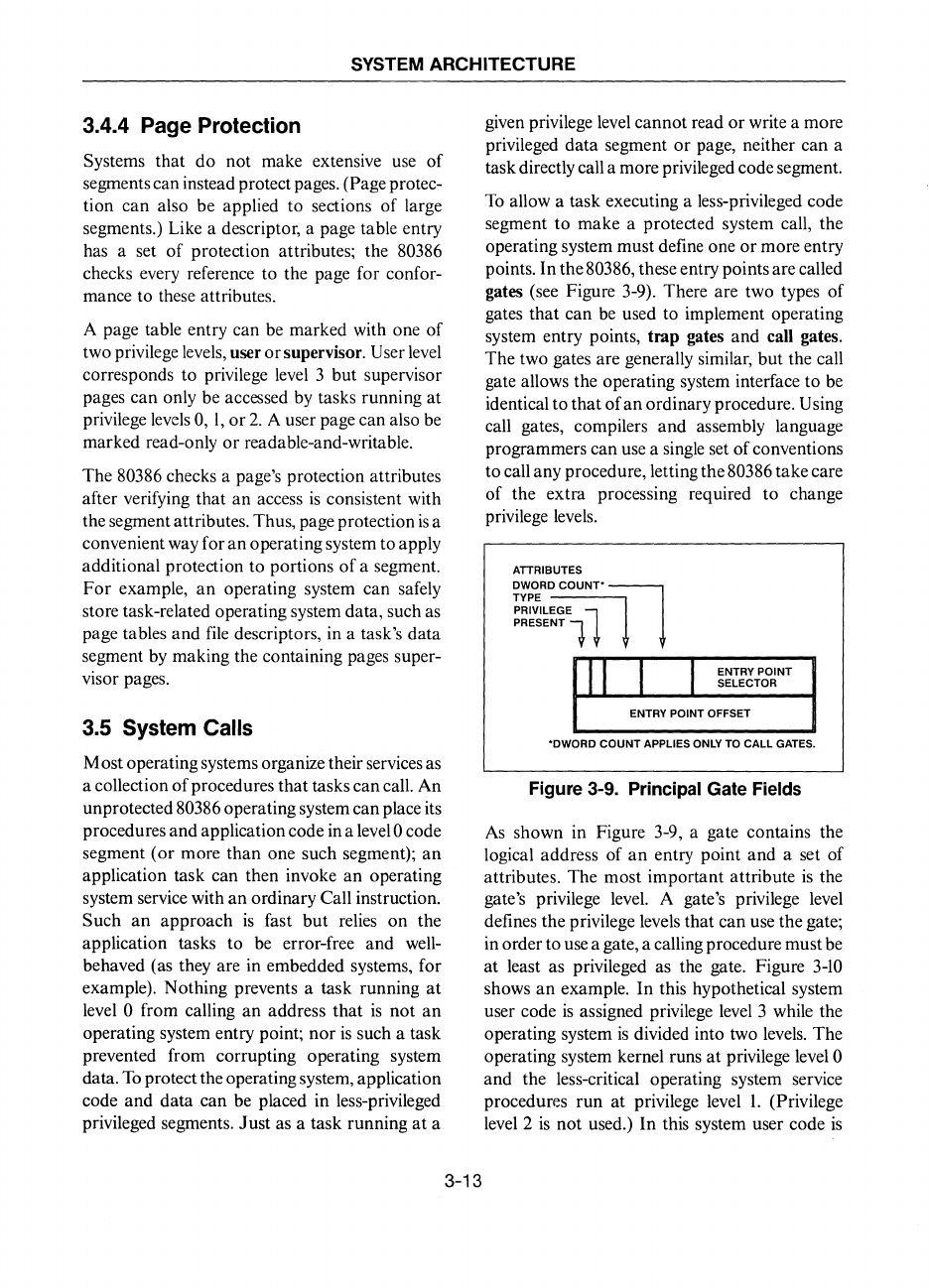
To
allow a task executing a less-privileged code
segment to make a protected system call, the
operating system must define one or more entry
points. In the
80386, these entry points are called
gates (see Figure 3-9). There are two types of
gates that can
be
used to implement operating
system entry points, trap gates and call gates.
The two gates are generally similar, but the call
gate allows the operating system interface to
be
identical to that of
an
ordinary procedure. Using
call gates, compilers and assembly language
programmers can use a single set of conventions
to call any procedure, letting the
80386 take care
of the extra processing required to change
privilege
levels.
ATTRIBUTES
DWORD
COUNP
n
TYPE~
PRIVILEGE 1
PRESENT 1
11
I
I
ENTRY POINT
SELECTOR
ENTRY POINT OFFSET
'DWORD COUNT
APPLIES ONLY TO CALL GATES.
Figure 3-9. Principal Gate Fields
As
shown in Figure 3-9, a gate contains the
logical address of
an
entry point and a set of
attributes. The most important attribute
is
the
gate's privilege level. A gate's privilege
level
defines the privilege levels that can use the gate;
in order to
use
a gate, a calling procedure must
be
at least as privileged
as
the gate. Figure
3-10
shows
an
example. In this hypothetical system
user code
is
assigned privilege
level
3 while the
operating system
is
divided into two
levels.
The
operating system kernel runs at privilege
level
0
and the less-critical operating system service
procedures run at privilege level
1.
(Privilege
level
2
is
not used.) In this system user code
is


















